Pig Butchering Crypto Scam Exposed: Fake Rich Friend Uses Deepfakes & Stolen Photos to Steal Billions
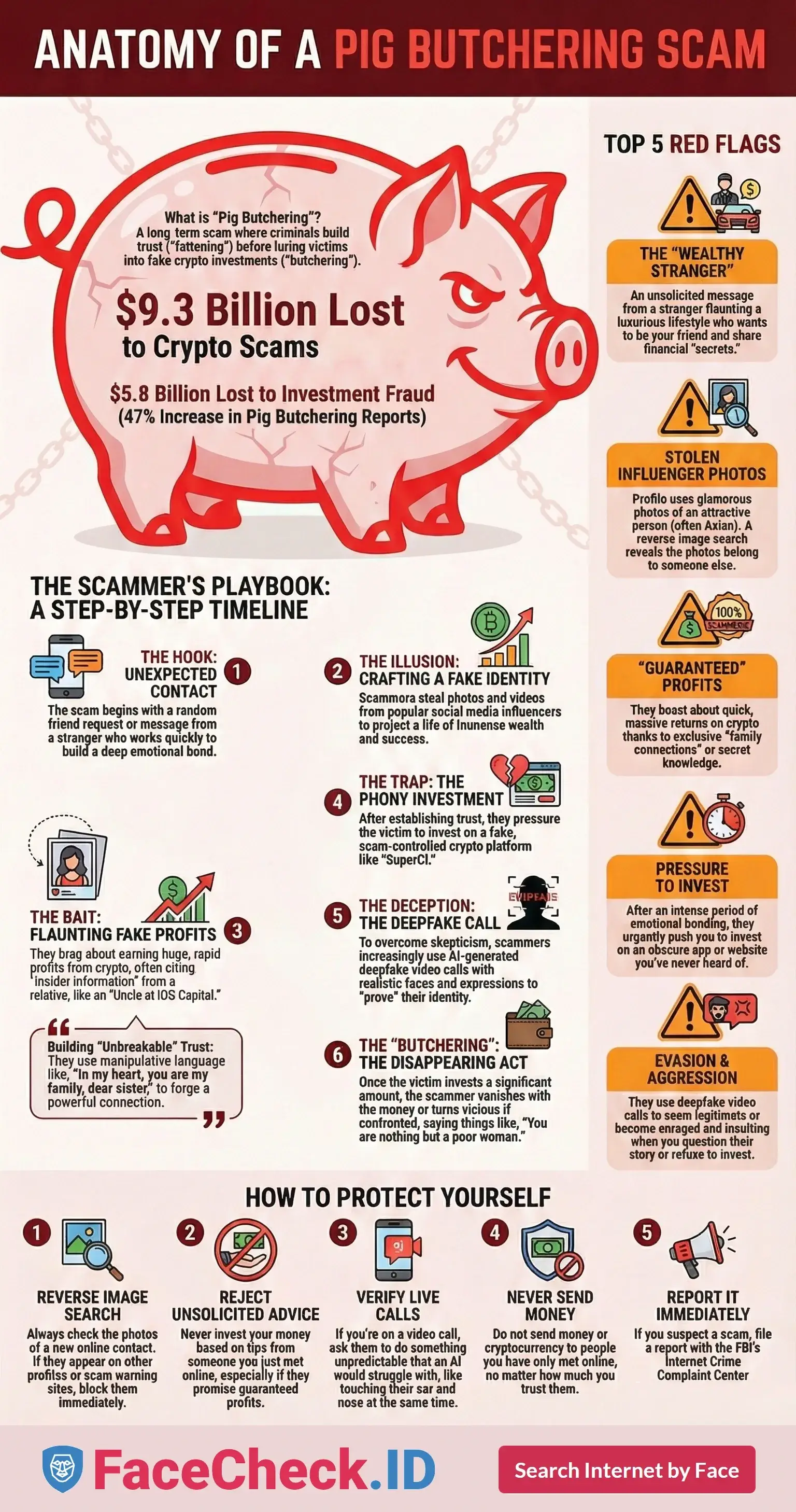
Last year, Americans lost a staggering $9.3 billion to cryptocurrency scams (FBI IC3 Report), with crypto investment fraud, including pig butchering schemes, driving $5.8 billion in losses, a 47% increase year-over-year. These scams continue surging into 2025, fueled by AI deepfakes and organized crime.
This undercover investigation exposes how pig butchering works: A fake "wealthy sister" steals photos of popular Chinese influencer Yangyang Sweet, flaunts luxury, builds unbreakable trust, then lures victims into bogus crypto platforms.
Top 5 Pig Butchering Scam Red Flags
- Sudden "friendship" from a wealthy stranger promising to share success.
- Stolen photos of attractive influencers (often Asian women in luxury).
- Bragging about rapid crypto profits via "family connections."
- Pressure to invest on unknown platforms after emotional bonding.
- Deepfake video calls or rage when confronted.
The "Unbreakable Friendship" That Started It All
A random connection request sparks messages from "Minlu" – claiming to be a New York cosmetics executive and UPenn grad with a lavish life.
She calls you "sister," shares "personal" charity, spa, Paris trip, and shopping photos. Offers advice, gifts, even Hawaii trips.
But it's engineered to spark envy and deep trust.
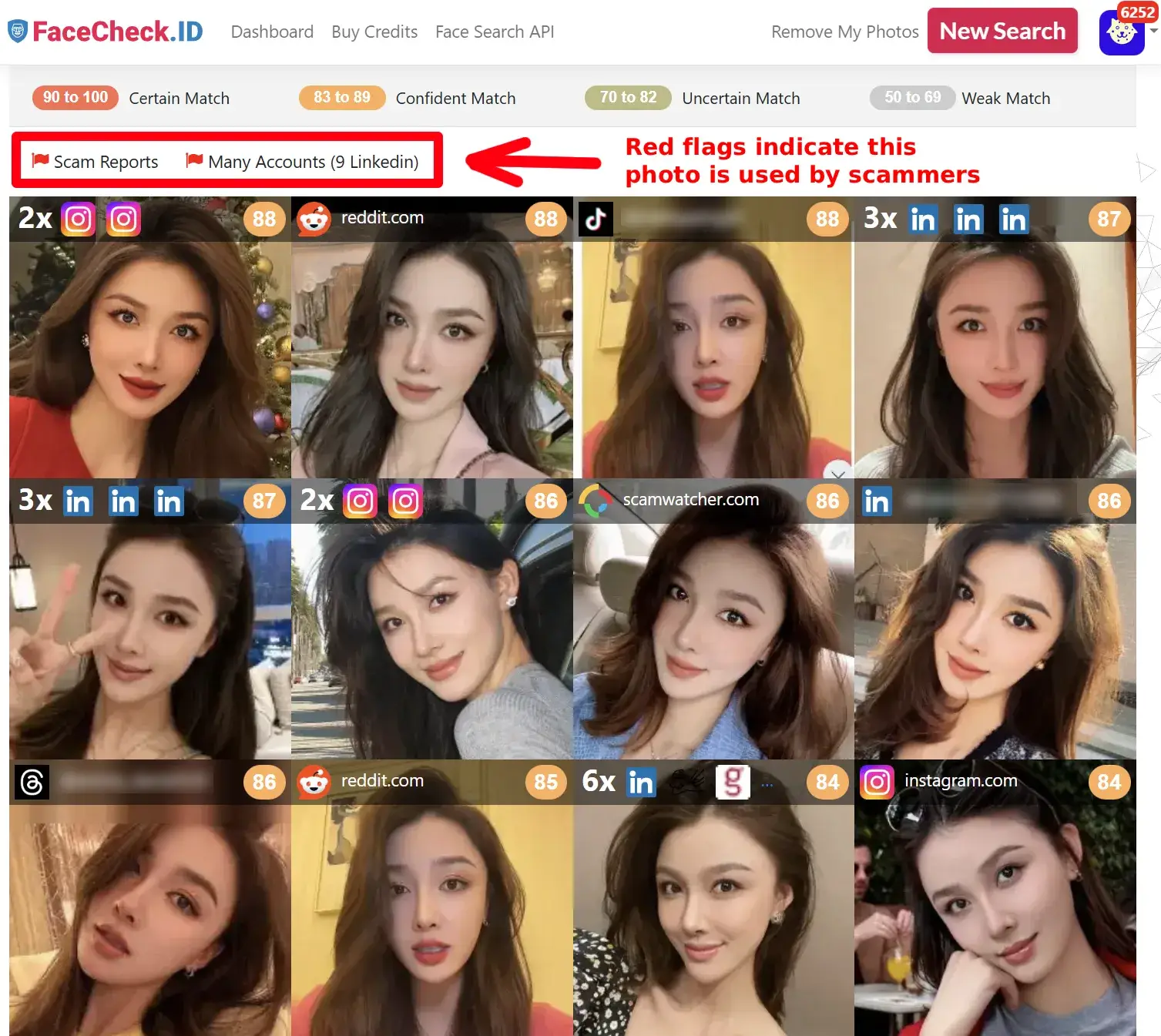
The Shocking Reveal: Stolen Photos Exposed
Scammers often steal photos of popular Asian influencers like Yangyang Sweet to create aspirational, believable profiles.
Reverse image searches reveal: The FaceCheck.ID reverse image search results provide clear confirmation that this pic is part of a scam. Red flags explicitly linking the photo to scam tracking websites indicate it's stolen and commonly used in fraud, while the appearance of nine different LinkedIn profiles all featuring the same person but under various names is a classic hallmark of organized scammers recycling identities to target multiple victims simultaneously.
The Classic Pig Butchering Playbook
"Minlu" uses the standard script:
- Rapid emotional bond – "In my heart, you are my family, dear sister."
- Wealth flaunting to inspire aspiration.
- "Uncle" at IDG Capital sharing crypto secrets.
- Fake profits demos ($53,000 in minutes).
- Step-by-step guidance to phony sites like SuperCI, demanding transfers/screenshots.
Deepfake Video Calls: The New Deception
To cement trust, "Minlu" uses live calls – often AI-generated deepfakes with realistic hands and expressions.
When Confronted: The Mask Slips
Challenge the lies? Sweet "sister" turns vicious: "You are nothing but a poor woman."
Account disappears – but photos reappear under new names (Andor, Bella, Yvonne, Amanda Mary).
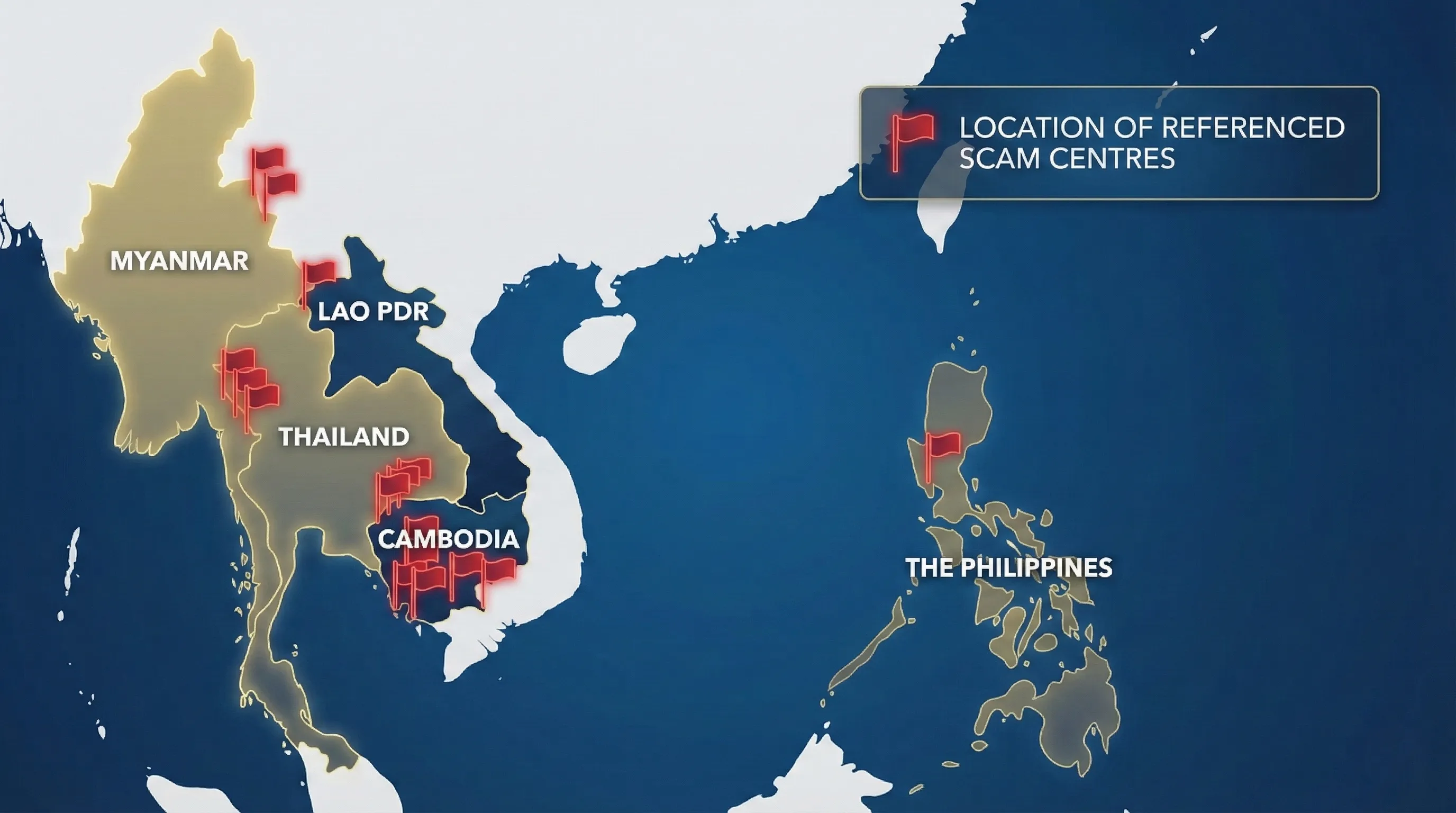
Behind the Scam: Human Trafficking Compounds
Many operators are trafficked victims forced into fraud at guarded Asian compounds.
Protect Yourself From Pig Butchering Scams
- Reverse image search every new contact's photos
- Never invest on unsolicited advice or "guaranteed" profits.
- Verify video calls with unpredictable questions.
- Avoid sending money/crypto to online contacts.
- Report the crime to the appropriate agency.
- United States: File a complaint with the Internet Crime Complaint Center (IC3)
- Canada: Report to the Canadian Anti-Fraud Centre
- United Kingdom: Report cybercrime to Action Fraud
- Australia: Submit a report via ReportCyber
- European Union: Report online crime through your country’s police authority or via Europol
- India: File a complaint on the National Cyber Crime Reporting Portal
- New Zealand: Report to CERT NZ
- Singapore: File a report with the Singapore Police Force – Scam Reporting
- Global / Other countries: Contact your local law enforcement agency
Suspect a fake profile? Share this article – it could protect someone's savings.
In this article, we're going to discuss
FAQ
What is a pig butchering scam?
A pig butchering scam is a long-term fraud where someone builds a close relationship with you first, then guides you into a fake investment, most often involving cryptocurrency, so they can eventually take your money.
Why is it called “pig butchering”?
The name comes from the scammer’s strategy of “fattening” a victim over time by building trust and confidence, encouraging small early steps, and slowly increasing the amount of money involved before stealing it all.
What is the fattening phase?
The fattening phase is the trust-building period where the scammer acts consistent, caring, and available so the relationship feels real. They message daily, remember details about your life, and often position themselves as successful and helpful, which makes later investment pressure feel like friendly advice instead of a sales pitch.
How long does the fattening phase last?
It can last weeks or months, and sometimes longer, because the scam works better when it feels unhurried. Scammers often mirror your pace and only turn up the pressure once you seem comfortable and emotionally invested.
What do scammers do during the fattening phase?
They try to become a normal part of your routine by chatting often, sharing personal stories, and creating a sense of closeness. They may also introduce a “success” narrative, like a great job, a wealthy lifestyle, or a special investing method, so the eventual pitch seems believable.
When does it turn into the investment pitch?
The pitch usually starts softly, like a casual mention of trading or a screenshot of profits, then builds into an offer to show you how to do it too. It often feels like they are doing you a favor, and they may frame it as a shared future plan or a way for you to feel secure.
Why do victims sometimes believe the platform is real?
Many fake platforms look polished and show convincing balances and charts, but the numbers are controlled by the scammer. Some victims are even allowed a small withdrawal early on, which makes the experience feel legitimate and increases trust.
What is the “butchering” part?
The “butchering” is when the scammer tries to extract the largest possible amount, often by pushing you to deposit more and more, then blocking withdrawals. They may claim you must pay extra for taxes, fees, or verification, and they keep moving the goalposts until you stop paying.
What are common red flags during the fattening phase?
A big warning sign is someone who quickly wants to move the conversation off the original app, keeps the relationship intense and constant, and repeatedly steers the topic toward money or crypto. Another red flag is any request for secrecy, urgency, or pressure to act before you can talk it over with someone you trust.
What should I do if I think I am in the fattening phase?
Slow things down and do not send money or personal financial details. Save screenshots and key info like usernames, phone numbers, website links, and any wallet addresses, because having a record helps if you need to report it.
How do I report a pig butchering scam?
Report it as soon as possible at ic3.gov and include all the details you have saved, especially transaction information and any wallet addresses. Quick reporting helps investigators connect patterns across cases and can improve the chances of disruption.
(Updated 2026 with latest FBI IC3 and Chainalysis trends)
Read More on Search by Selfie
Unlocking the Power of Facial Recognition Technology: 10 Eye-Opening Facts
Facial recognition now tops 99% accuracy, but how does it actually work, and what are the hidden limitations no one talks about? From detecting emotions to identifying disguised individuals, these 10 facts reveal what the technology can really do and the biases that could affect you.
Popular Topics
Deepfake Video Deepfake Identity Image Search Reverse Image Search How To LinkedIn Scammers Fake Profiles Law Enforcement Screenshot Pig ButcheringReverse Image Search Showdown 2026: PimEyes vs FaceCheck - Who Wins?