North Korea It Worker Scheme: Explained + Red Flags
Definition
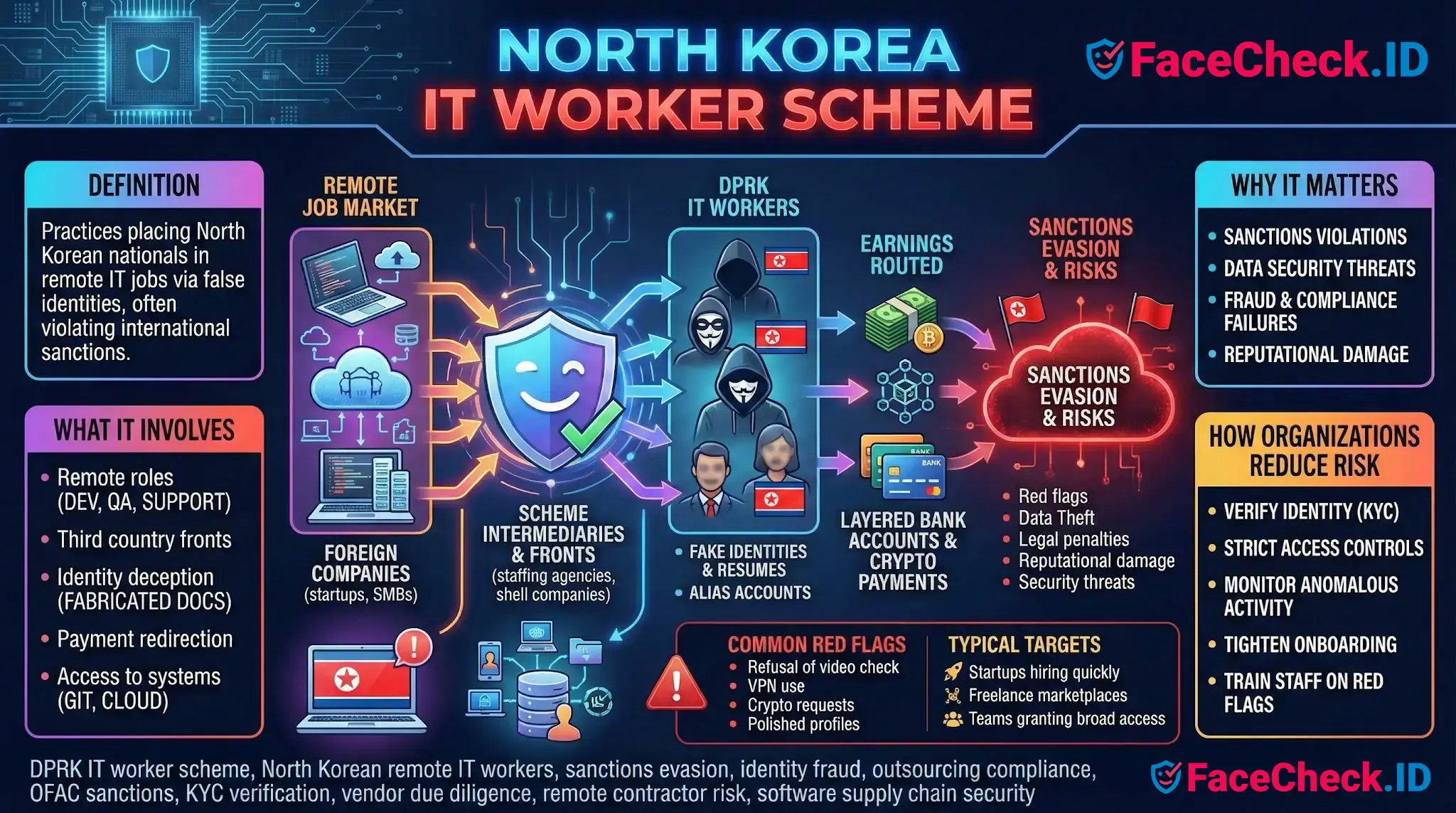
North Korea It Worker Scheme refers to a set of practices used to place North Korean nationals in remote information technology jobs for foreign companies, often through intermediaries and false identities. The work is typically presented as standard offshore development or IT support, but earnings may be routed in ways that can violate international sanctions and create legal, financial, and security risks for the hiring organization.
What it usually involves
- Remote roles such as software development, web development, mobile apps, QA testing, DevOps, data tasks, or IT support
- Use of third country fronts like staffing agencies, outsourcing vendors, or shell companies
- Identity deception such as fabricated resumes, stolen identities, alias accounts, or manipulated KYC documents
- Payment redirection through layered bank accounts, crypto payments, or invoice laundering
- Access to company systems like Git repositories, cloud environments, CI pipelines, and internal admin tools
Why it matters
Hiring through a North Korea It Worker Scheme can expose an organization to:
- Sanctions violations, including penalties for providing funds or services to sanctioned parties
- Data security threats such as credential harvesting, source code theft, or persistent access
- Fraud and compliance failures, including inaccurate vendor onboarding and employment records
- Reputational damage and incident response costs if discovered by customers, banks, or regulators
Common red flags
- Refusal or inability to complete reliable identity verification or live video checks
- Inconsistent location signals, frequent VPN use, or time zone contradictions
- Requests to be paid in crypto, to different names, or via unusual invoicing structures
- Multiple applicants sharing similar portfolios, writing style, or reused project histories
- Overly polished profiles with limited verifiable employment history
- Unusual pressure for broad system access early in the engagement
Typical targets
- Startups and SMBs hiring quickly for remote engineering roles
- Companies using freelance marketplaces or low cost outsourcing vendors
- Teams granting contractor access to production, cloud consoles, or financial systems
- Organizations without strong vendor due diligence and identity verification
How organizations reduce risk
- Verify identity and location using reliable KYC processes and consider in person or notarized checks for sensitive roles
- Use strict least privilege access, separate contractor environments, and time bound credentials
- Monitor for anomalous logins, impossible travel patterns, and unusual repository activity
- Tighten vendor onboarding, beneficial ownership checks, and payment controls
- Train recruiters and hiring managers to recognize identity and payment red flags
- Consult legal and compliance experts for sanctions screening and reporting obligations
Related terms and alternative names
This topic is also described as North Korean remote IT worker fraud, DPRK IT worker scheme, sanctions evasion via IT contracting, and North Korean developer scam.
FAQ
What does the term “North Korea IT Worker Scheme” refer to in the context of face recognition search engines?
In this context, “North Korea IT Worker Scheme” is typically used to describe suspected remote-work fraud where an individual’s real identity, location, or employment eligibility may be misrepresented (including by using stolen, borrowed, or synthetic profile photos). Face recognition search engines are sometimes used as a screening aid to check whether the same face appears across unrelated profiles, aliases, or scam/fraud-report pages—without treating any match as proof.
How can a face recognition search engine help evaluate whether a job candidate photo might be stolen or reused across fake identities?
A face search can surface where the same face appears online, which may reveal patterns consistent with photo misuse: the identical face tied to multiple names, conflicting biographies, or reused headshots across many accounts. Tools such as FaceCheck.ID (and similar open-web face search engines) can provide leads to investigate, but you should corroborate with non-biometric checks (work history validation, references, domain email verification, live technical interview) before drawing conclusions.
What face-search result patterns should be treated as higher-risk signals in “North Korea IT worker scheme” discussions (without assuming guilt)?
Higher-risk signals are usually about inconsistency and reuse, not nationality: (1) one face matched to many different names/usernames across platforms; (2) the same headshot appearing on “for hire” profiles with incompatible skills, time zones, or employment histories; (3) repeated use of identical or near-identical profile photos across multiple newly created accounts; (4) matches that lead to obvious impersonation reports or takedown posts. Any of these can also have benign explanations (reposts, modeling portfolios, scraped images), so treat them as prompts for verification.
What are the main limitations of using face recognition search to investigate a suspected “North Korea IT Worker Scheme” profile?
Face search is not identity proof and can be wrong due to look-alikes, low-quality images, heavy edits/filters, AI-generated faces, or outdated indexed pages. It also may miss matches if the person’s images are not publicly accessible or not indexed. Use results as investigative leads, document uncertainty, and avoid making employment decisions based solely on a face-match result.
If a face-search tool returns matches suggesting photo reuse in a hiring workflow, what is a safer, practical next step sequence?
A safer workflow is: (1) Save links/screenshots of the relevant matched pages and note dates/context; (2) Look for consistency across independent signals (same name, same work history, same public portfolio) rather than relying on face similarity alone; (3) Perform a live video verification step appropriate to your policy (e.g., real-time interview, role-specific technical screen) and verify employment eligibility through standard HR/legal processes; (4) If impersonation is likely, request clarification from the candidate and escalate to internal security/HR for policy-based handling; (5) If your own company’s or employee’s images are being misused, pursue takedowns/impersonation reports on the hosting platforms.

Recommended Posts Related to north korea it worker scheme
-
How to Detect Fake Remote IT Workers with Facial Recognition (2026 Guide)
Nov 14, 2025 — United States DOJ announces indictments in major North Korean IT-worker scheme.