Open-Source Intelligence (OSINT) Explained
Definition
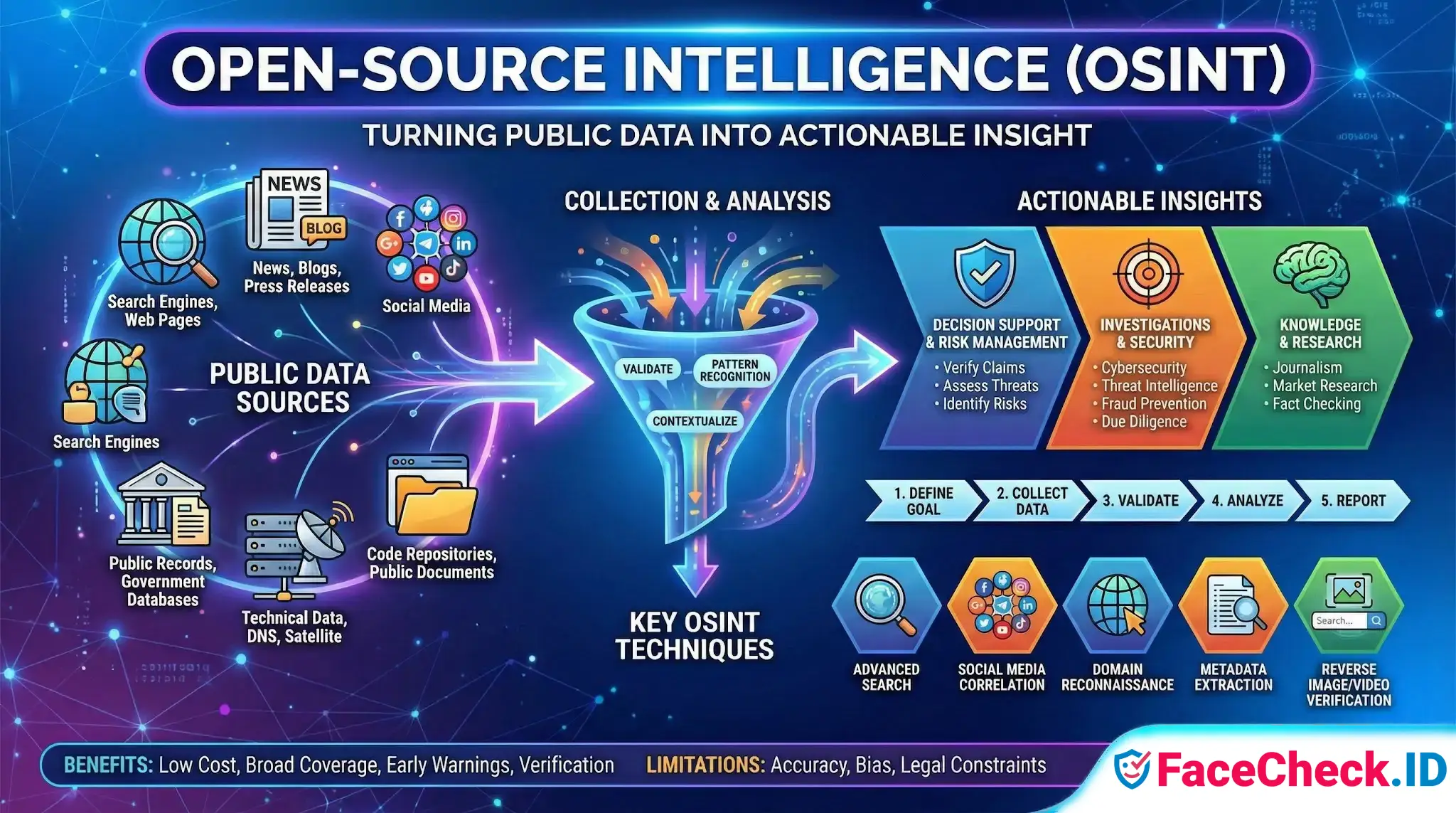
Open-Source Intelligence (OSINT) is the practice of collecting, analyzing, and using information that is legally available to the public to support decisions, investigations, and risk management. OSINT turns public data into actionable insight.
What counts as open source
Open source does not mean open source software. In OSINT, open source means information that anyone can access without breaking laws or bypassing access controls.
Common open sources include:
- Search engines and web pages
- News sites, blogs, and press releases
- Social media posts, profiles, and public groups
- Public records and government databases
- Company websites, job postings, and filings
- Technical data like DNS records, IP addresses, certificates, and metadata
- Code repositories and developer forums
- Images, videos, and publicly shared documents
- Maps, satellite imagery, and location data
How OSINT works
A typical OSINT workflow includes:
- Define the goal, such as verifying a claim or assessing a threat
- Collect relevant public data from multiple sources
- Validate information by cross checking sources and timestamps
- Analyze relationships, patterns, and context
- Report findings clearly, with sources and confidence levels
Key OSINT techniques
- Advanced search queries and filters
- Social media and username correlation
- Domain and network reconnaissance using public data
- Metadata extraction from files and media
- Reverse image and video verification
- Timeline building and geolocation
- Entity resolution, matching identities across platforms
OSINT use cases
OSINT is used across many fields:
- Cybersecurity: identifying exposed assets, brand impersonation, leaked credentials, and attacker infrastructure
- Threat intelligence: tracking tactics, campaigns, and indicators from public reporting
- Fraud prevention: spotting fake identities, mule accounts, and suspicious patterns
- Due diligence: assessing companies, executives, and business relationships
- Journalism and research: verifying events, sources, and claims
- Law enforcement and investigations: locating leads and corroborating evidence within legal limits
- Physical security: assessing event risk and monitoring public threats
OSINT vs related concepts
- OSINT vs HUMINT: HUMINT comes from human sources and interviews, OSINT comes from public information
- OSINT vs SIGINT: SIGINT involves intercepted signals, OSINT avoids interception and relies on legal public access
- OSINT vs reconnaissance: reconnaissance is a broader term, OSINT is specifically public source intelligence gathering
- OSINT vs data scraping: scraping is a collection method, OSINT includes analysis and verification, and must be lawful
Benefits of OSINT
- Low cost compared to proprietary intelligence sources
- Broad coverage across technical, social, and business signals
- Faster early warnings for emerging risks
- Useful for verification and fact checking
Limitations and risks
- Accuracy issues, misinformation, and outdated content
- Bias from incomplete or one sided sources
- Identity mix ups when names and usernames overlap
- Legal and ethical constraints, especially around privacy
- Data can disappear quickly, requiring careful documentation
Legal and ethical considerations
OSINT should be conducted with respect for privacy, terms of service, and local laws. Avoid accessing non public data, bypassing authentication, or using deceptive methods that violate rules. When sharing findings, limit personal data and cite sources responsibly.
Examples
- A security team finds a leaked API key in a public code repository and removes it, then rotates credentials.
- An investigator verifies a video location using landmarks, map data, and upload timestamps.
- A risk team reviews a vendor using public filings, breach reports, and domain records.
Related tools and platforms
OSINT can be done with simple tools like search engines and spreadsheets, as well as specialized platforms for link analysis, threat intelligence, and digital forensics. The best approach is usually a mix of manual verification and targeted tooling.
FAQ
What does “Open-Source Intelligence (OSINT)” mean when using face recognition search engines?
Open-Source Intelligence (OSINT) is the practice of collecting and analyzing information from publicly available sources. In the context of face recognition search engines, OSINT typically means using face-match results as leads to discover where a face image appears online (e.g., public webpages, reposts, news pages, forums), then validating those leads with additional open-source checks rather than treating a match as proof of identity.
What are common OSINT workflows after you get results from a face recognition search engine?
Common OSINT workflows include: (1) open the result URLs and confirm the face context (same person vs look-alike), (2) trace the earliest/most authoritative source (original upload vs reposts/screenshots), (3) corroborate with non-face indicators such as consistent usernames, timestamps, locations, and cross-links, (4) run parallel checks (reverse image search for duplicates, keyword searches for handles), and (5) document findings with links and dates while keeping conclusions tentative unless independently verified.
How do OSINT analysts reduce misidentification risk when using face recognition search engines?
They treat face matches as hypotheses, not identifications; verify with multiple independent sources; look for consistency across time (age progression, recurring context); compare multiple photos of the same subject rather than relying on a single image; be cautious with low-quality, filtered, or AI-generated images; and avoid making high-stakes claims (accusations, doxxing, reporting) unless there is strong corroboration beyond the face similarity.
What kinds of open sources can bias or distort OSINT conclusions from face-search results?
Open sources can be misleading due to repost networks, meme pages, aggregators, scraped “public record” and mugshot-style sites, fan pages, and mislabeled uploads. These sources can create false associations (e.g., attaching a face to the wrong name or story), so OSINT practice emphasizes checking primary/earliest sources, evaluating credibility, and confirming context rather than trusting the first matching page.
How can FaceCheck.ID add value in an OSINT workflow for face recognition search engines?
In an OSINT workflow, FaceCheck.ID can be used as one lead-generation step to locate webpages where a similar face appears. The value is in widening discovery (finding candidate pages to review) and enabling cross-checking against other tools and open-source indicators. As with any face search engine, results should be validated by reviewing the linked pages and corroborating with additional OSINT evidence before drawing conclusions about identity.

Recommended Posts Related to open-source intelligence
-
Leveraging Facial Recognition Technology to Combat Human Trafficking
The Impact of Open-Source Intelligence (OSINT) on Human Trafficking Cases. Combining facial recognition with open-source intelligence (OSINT) significantly enhances the efficiency of investigations. Open-Source Intelligence (OSINT) Analysis.
-
How to Find Anyone Online: A Comprehensive Guide to Internet Sleuthing
TheHarvester: TheHarvester is an open-source intelligence gathering tool designed to help collect information about email addresses, subdomains, and other data related to a target.

