Impersonation Explained: Signs, Types & Protection
Impersonation is when someone pretends to be another person, brand, or organization to gain trust, access accounts, steal money, collect personal data, or damage a reputation. It can happen online or offline, but it is especially common in email, social media, phone calls, and messaging apps.
What impersonation looks like
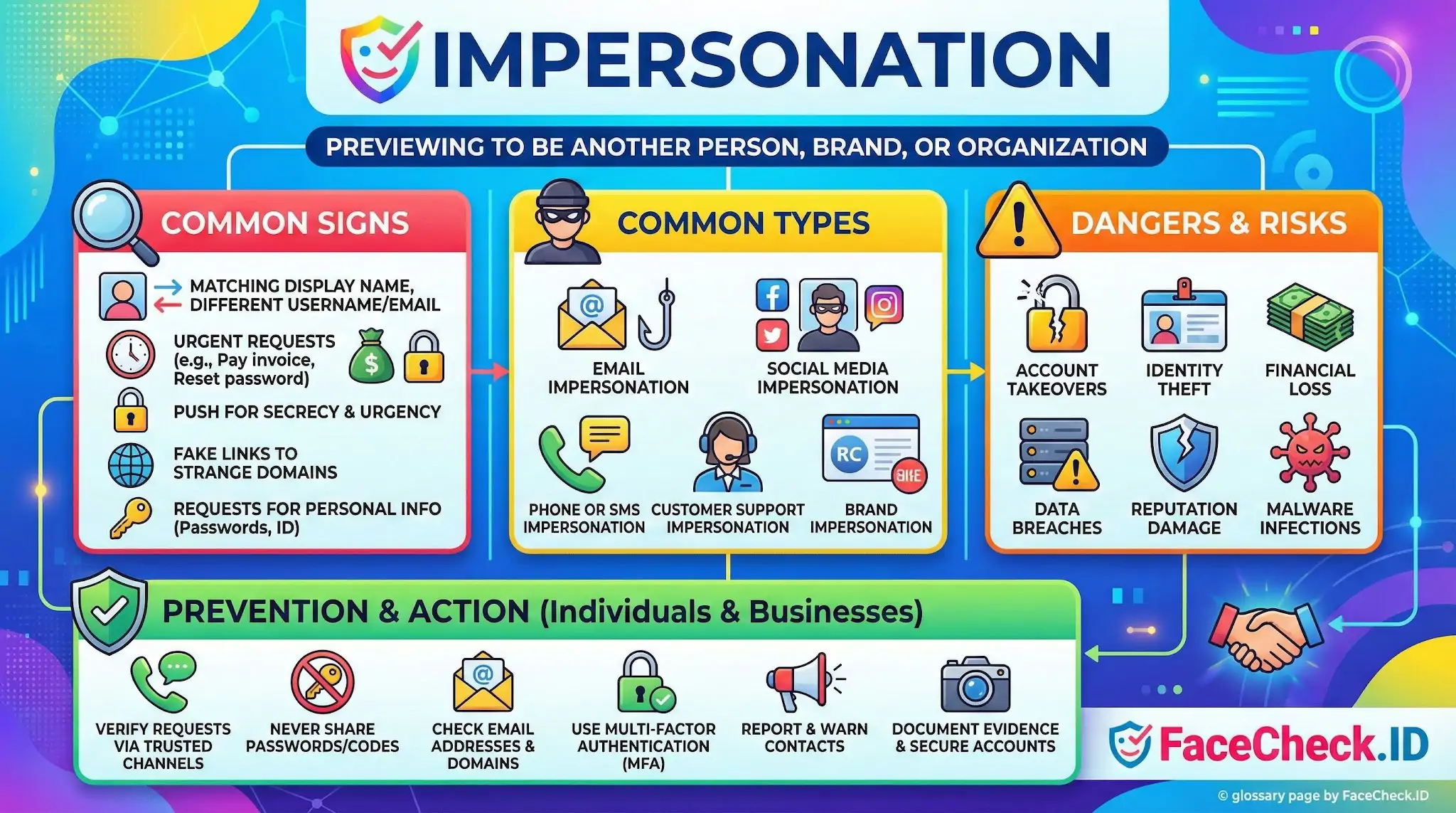
Impersonation often tries to copy familiar details so the target does not question it. Common signs include:
- A display name or profile photo that matches a real person or company, but the username, email address, or URL is slightly different
- Urgent requests such as pay an invoice, reset a password, share a code, or send gift cards
- Messages that push secrecy like do not tell anyone or handle this right now
- Links to login pages that look real but have a strange domain
- Requests for personal information like passwords, one time passcodes, bank details, or ID documents
Common types of impersonation
Email impersonation
A sender makes an email look like it came from a trusted person or business. This is often tied to phishing and business email compromise.
Social media impersonation
A fake account copies a real profile, then messages followers to ask for money, promote scams, or spread misinformation.
Phone or SMS impersonation
A caller or texter claims to be from a bank, delivery company, tax office, or employer. This can include caller ID spoofing.
Customer support impersonation
Scammers pose as support agents to trick users into sharing login codes or installing remote access software.
Brand impersonation
Fraudsters create lookalike websites, ads, or accounts using a company name and logos to steal payments or customer data.
Why impersonation is dangerous
Impersonation can lead to:
- Account takeovers
- Identity theft
- Financial loss through fraudulent payments
- Data breaches and leaked credentials
- Reputation damage to individuals and businesses
- Malware infections from fake links or attachments
Impersonation vs related concepts
- Impersonation vs phishing: Impersonation is the act of pretending to be a trusted identity. Phishing is the broader tactic of using deceptive messages to steal information or money. Impersonation is a common phishing method.
- Impersonation vs spoofing: Spoofing is faking technical identifiers like an email header, phone number, or domain. Impersonation focuses on pretending to be a specific person or brand. Many scams use both.
- Impersonation vs identity theft: Impersonation is the behavior of posing as someone. Identity theft is stealing and using someone’s personal data, often as a result of impersonation.
How to prevent impersonation
For individuals
- Verify requests using a trusted channel, like calling the official number on a company website
- Never share passwords or one time passcodes, even with someone claiming to be support
- Check email addresses, domains, and usernames carefully for small changes
- Use multi factor authentication and a password manager
- Avoid clicking login links in unexpected messages, type the site address instead
For businesses
- Enforce multi factor authentication on email and admin accounts
- Use email authentication protocols like SPF, DKIM, and DMARC
- Monitor for fake social profiles and lookalike domains
- Train staff to confirm payment or bank detail changes with a second approval
- Provide clear support channels so customers know how to contact you safely
What to do if you are being impersonated
- Report the account or message to the platform, email provider, or phone carrier
- Warn contacts through your official channels
- Document evidence with screenshots, URLs, and timestamps
- Secure accounts by changing passwords and enabling multi factor authentication
- If money or sensitive data was involved, contact your bank and local authorities
FAQ
What does “Impersonation” mean in the context of face recognition search engines?
In face recognition search engines, “impersonation” typically means someone is using another person’s face photo(s) to present themselves as that person (or to appear connected to them) on a profile, listing, forum post, scam page, or other online content. The goal is usually to borrow trust, avoid detection, or mislead others—rather than merely sharing or reposting a photo.
What face-search result patterns most strongly suggest photo-based impersonation (not just reposting)?
Common impersonation clues include: (1) the same face photo appearing across multiple accounts with different names/usernames, (2) a profile using a face photo but inconsistent biographical details (age, location, job) across sources, (3) the “oldest” or most authoritative-looking source (e.g., an established personal site or long-running profile) not matching the newer account’s identity claims, and (4) a cluster of near-identical images used repeatedly in different contexts (dating, crypto, classifieds) that resemble scam reuse patterns.
If a face recognition search engine shows my face on an account I don’t control, what should I do first?
First, preserve evidence (screenshots, URLs, timestamps), then try to confirm it’s truly your image (compare unique features, original photo set, and context). Next, report the content to the platform using its impersonation/reporting workflow and request takedown. If the post is tied to fraud, harassment, or extortion, consider notifying relevant service providers (payment apps, marketplaces) and—if needed—local authorities. Avoid directly confronting the impersonator if it could escalate risk.
How can I reduce false accusations when investigating suspected impersonation with face search results?
Treat face-search matches as leads, not proof. Validate using multiple, independent signals: check whether the matched pages show consistent identity details over time, look for cross-links from official accounts, compare multiple photos (not just one), and verify context (captions, dates, location cues, and whether the page is a repost/screenshot archive). If uncertainty remains, don’t publish allegations; instead, report to the platform with evidence and describe the mismatch without claiming certainty.
How can FaceCheck.ID add value in an impersonation investigation, and what’s the safest way to use it?
FaceCheck.ID can help by quickly surfacing where a face appears across publicly accessible pages, which can reveal duplicate use of the same headshot across different profiles—often a useful indicator when checking for impersonation or stolen photos. The safest approach is to use it to map reuse patterns (where the face appears, how often, and in what contexts), then verify each hit at the source page and document discrepancies. Don’t rely on a single result or similarity score to conclude someone’s identity or intent.

Recommended Posts Related to impersonation
-
Celebrity Romance Scams 2026: How Scammers Use AI Deepfakes and Stolen Photos to Steal Millions
Warning: Romance scammers are using AI-generated images, deepfakes, and celebrity impersonations to target victims in 2026. The Rising Threat of Celebrity Impersonation Romance Scams in 2026. Scammers impersonate celebrities to build trust, exploit emotions, and defraud victims—often older adults—of life-changing sums.
-
Fake Profile Scam? Why 99% of the Time the Person in the Photo Is Innocent
This profile is impersonating someone and using stolen photos. Impersonation scams. This account is impersonating someone.
-
Elder Fraud Statistics 2025: FTC Reports $2.4 Billion Lost to Scams Targeting Seniors
Investment scams, romance scams, and government impersonators are the biggest threats. 🏛️ Government Impersonation Scams. 🚨 The FTC Impersonator Epidemic.
-
140+ Common Romance Scammer Lines, Excuses & Red Flags to Watch For in 2026
In 2026, romance scams remain a top threat, with older adults (60+) reporting $2.4 billion in total fraud losses (often driven by investment scams, romance scams, and impersonation frauds) ftc.gov. A scammer impersonates a celebrity (or someone “on their team”), builds emotional trust fast, then introduces secrecy and a payment hook—VIP passes, “fan club” fees, travel costs, verification fees, gift cards, or crypto.
-
How to Spot a Catfish in 2025: Red Flags in Fake Dating Profiles
lost $270,000 on Match.com when a scammer impersonated a former diplomat.
-
How to Detect Fake Remote IT Workers with Facial Recognition (2026 Guide)
Post-Phone ScreenRequest fresh selfie uploadCatch impersonation and deepfake attempts45 sec. Deepfake video impersonators.
-
Facial Recognition: Understanding the Basics
It protects against techniques like using photos, videos, or sophisticated 3D masks to impersonate authorized individuals.
-
What is The Most Accurate Reverse Image Search?
Its specialized algorithms and focus on facial recognition ensure that impersonators can be swiftly identified.