Identification Explained: Meaning & Digital Examples
Identification is the process of recognizing and distinguishing a person, object, or item based on specific features or characteristics. In digital systems, identification means using data to determine what something is or who someone is.
How identification works in digital contexts
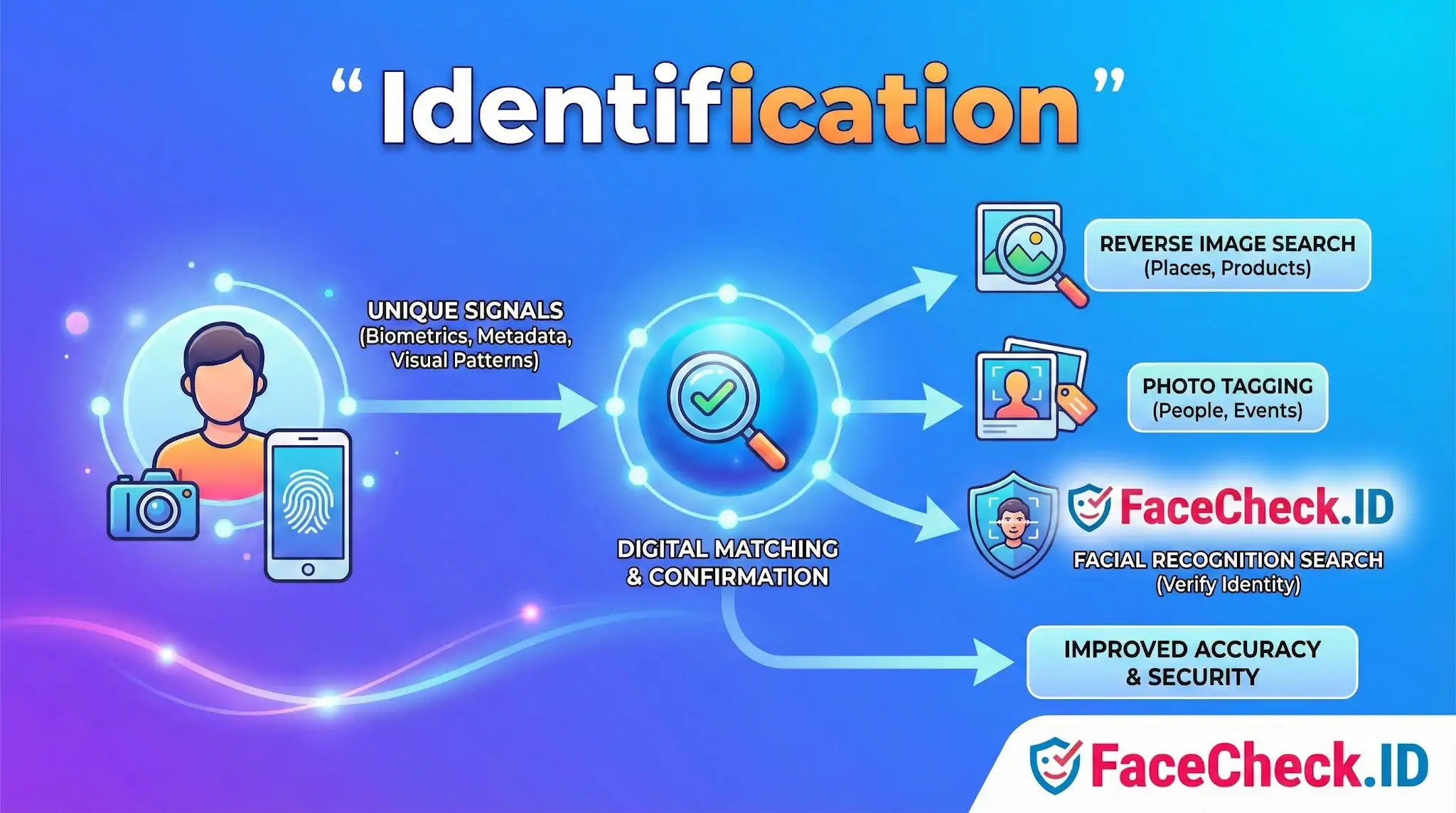
Identification often relies on unique signals such as visual patterns, metadata, device details, or biometric traits. Systems compare these signals to known references to label, match, or confirm an identity.
Common examples of identification
- Reverse image search: Identifies what an image contains, such as a person, place, product, logo, or scene, then returns visually similar or related results.
- Social media photo tagging: Identifies people in photos so they can be tagged, often using face detection and facial recognition.
- Facial recognition search: Uses biometric facial features to identify a person or verify that a person matches a claimed identity.
Why identification matters
Identification helps improve search accuracy, content organization, security checks, and user experiences across platforms that handle images, videos, and large datasets.
FAQ
What does “Identification” mean in the context of face recognition search engines?
In face recognition search engines, “identification” usually means trying to determine who a person is by finding likely online appearances of a similar face and then inferring an identity from the surrounding context (names, usernames, profiles, captions). A face match alone is not an identification; it’s a lead that may or may not support an identity claim.
How do face recognition search results contribute to identifying a person if they don’t return a verified name?
They can support identification indirectly by linking to webpages where the person may be named or consistently associated with the same account. Identification typically comes from corroborating evidence across multiple independent sources (same face, same handle, same location or affiliations), not from a single match.
What is “open-web identification” and why is it riskier than identifying someone in a controlled database?
Open-web identification uses public internet content that may be incomplete, outdated, mislabeled, or reposted without context. Unlike controlled databases (e.g., employee IDs), web sources often lack reliable ground truth, increasing the risk of misidentifying someone due to look-alikes, wrong tags, or recycled profile photos.
What are common ways face recognition searches can lead to false identification?
Common causes include doppelgängers/look-alikes, low-quality or angled photos, heavy filters/edits, AI-generated faces, incorrect captions or tags on webpages, reposted images attributed to the wrong person, and assuming that a profile link equals the person in the photo. Treat results as hypotheses and verify with additional evidence.
How can I use FaceCheck.ID (or similar tools) for identification more responsibly?
Use results as starting points only: check multiple high-confidence matches, open the source pages and verify context, look for consistent identifiers (same username, repeated photos across time), and avoid making accusations or decisions based on one hit. If the stakes are high (employment, legal, safety), use non-biometric verification methods and follow applicable laws and platform policies.

Recommended Posts Related to identification
-
Top 5 Reverse Image Search APIs for Your Projects
Reverse image search technology is vital in various areas, such as detecting copyright infringement, fraud prevention, people and product identification, image grouping and tagging, and enhancing search functionality. Reverse image search APIs offer efficient and precise image matching and identification, essential for intel gathering applications. Whether it's FaceCheck.ID for facial recognition or Google Cloud Vision for product identification, each API offers specific strengths.
-
Facial Recognition Resources
Facial recognition technology measures and matches the unique characteristics for identification or authentication. British Airways brings its biometric identification gates to three more US airports. These "biometric e-Gates," which have been on a trial at Los Angeles International Airport (LAX) since November 2017, use facial recognition to match flyers with their passport, visa, or immigration photos and can remove the need to show a boarding pass or identification when getting on a plane.
-
All About Face Recognition Technology
The technology is also sometimes called facial recognition or biometric identification. Biometric identification is any technology that identifies a person based on a physical or behavioral trait.
-
How to Enhance a Low-Resolution Blurry Face like a CSI Detective
Limitations in People Identification and Face Restoration. This limitation is particularly significant in forensic contexts or scenarios where precise identification is critical. AI-generated facial enhancements should therefore not be solely relied upon for definitive identification or restoration, necessitating additional evidence or verification methods.
-
How to Search Arrest Records and Mugshots by a Photo of a Person
Mugshots are one of law enforcement's most popular forms of identification. This could be due to new privacy laws or because law enforcement decides they are not an effective form of identification.
-
Reverse Image Search FAQ: The Ultimate Guide for 2025
Use specialized tools for celebrity or known face identification in videos. For face identification, use a clear frame showing the face and try FaceCheck.ID. FaceCheck.ID (optimal for face and person identification).
-
Facial Recognition: Understanding the Basics
Other biometric identification technologies include fingerprint analysis, voice recognition, DNA testing, and retinal scans. Other types of biometric identification technology? The process includes detecting faces, extracting facial vectors and features to create a faceprint, and matching it against existing faceprints for identification purposes.
-
Unlocking the Power of Facial Recognition Technology: 10 Eye-Opening Facts
Facial recognition can be used for a wide range of applications, including security, law enforcement, marketing, and personal identification. And in personal identification, facial recognition technology can be used to unlock smartphones, secure online accounts, and more.
-
Google's Image Search vs. Yandex's Image Search: A Detailed Look
Algorithms are trained by matching and unmatched photo triplets to optimize facial measurements and identification accuracy, though performance varies. Obscurity allows people to live authentic, multifaceted lives across different contexts that facial recognition's identification threatens to collapse.
-
Leveraging Facial Recognition Technology to Combat Human Trafficking
They frequently move between states, using aliases, fake IDs, and unregistered vehicles, making traditional identification methods ineffective. Similarly, images of traffickers can be matched with previous booking photos, aiding in their identification and capture. This technology can be a game-changer in situations where victims lack proper identification.
-
Uncover the Truth Before Your First Date
Identification of Scammers and Sex Offenders.
-
Doppelgänger Effect in Facial Recognition Technology
This could include checking their identification documents, asking questions, or using biometric methods, such as fingerprint or iris scanning.
-
Search for Actors by their Face
Character identification in movies and TV shows: We've all had that moment when a character appears on screen, and we just can't place them.
-
Searching Instagram by Photo: A Guide to Finding People and Accounts
Google offers similar images and detailed identification.
-
How to Search Instagram by Image
Before discovering FaceCheck.ID, I tried other methods like manually scrolling through Instagram, using generic search engines, or even crowd-sourcing identifications through social media.
-
How to Find Someone's Instagram Without Knowing Their Username
High-quality images and a significant online presence can enhance the likelihood of accurate identification.
-
Top 6 Reverse Image Search Mobile Sites to Find People, Products, and Places
The algorithm's blend of accuracy, speed, and robustness ensures that users get reliable results quickly, making it a go-to platform for individual identification.
-
How to Find and Remove Nude Deepfakes With FaceCheck.ID: A Step-by-Step Guide
Create emergency contact procedures that don't rely solely on voice identification.
-
Examining the State-of-the-Art in Facial Recognition Algorithms for Unconstrained Environments
The algorithm achieves state-of-the-art performance on standard benchmarks such as LFW and is used for various applications such as face identification and verification.